Fortinet (NASDAQ: FTNT), a network security solution provider, confirmed that it has been invaded by a malicious actor, resulting in a disclosure of SSL-VPN access information to 87,000 FortiGate SSL-VPN devices.
The affected company further added in their press release, “These credentials were obtained from systems that remained unpatched against FG-IR-18-384 / CVE-2018-13379 at the time of the actor’s scan. While they may have since been patched, if the passwords were not reset, they remain vulnerable.”
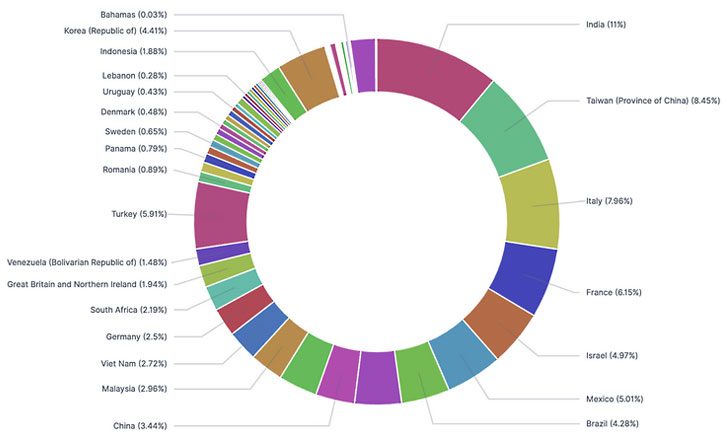
According to researchers, the breach list contains explicit access to high-profile companies from 74 countries, including – India, Taiwan, Italy, France, and Israel. Total number of affected U.S. entities are estimated to be 2,959 out of 22,500.
Fortinet customer support bulletin recommends its users to change passwords and perform upgrades even if they’re using up to date devices. Failure in doing so may cause post-upgrade vulnerabilities if users’ credentials were previously compromised.
*Image source: The Hacker News
Furthermore, Fortinite encourages users to immediately take the following steps:
- Disable all VPNs (SSL-VPN or IPSEC) until the following remediation steps have been taken.
- Immediately upgrade affected devices to the latest available release, as detailed below.
- Treat all credentials as potentially compromised by performing an organization-wide password reset.
- Implement multi-factor authentication, which will help mitigate the abuse of any compromised credentials, both now and in the future.
- Notify users to explain the reason for the password reset and monitor services such as HIBP for your domain. There is the potential that if passwords have been reused for other accounts, they could be used in credential stuffing attacks.
You can also use this link to learn details about Fortinet’s current PSIRT Policy and how to submit a potential vulnerability to the PSIRT team.

